In it we make active connections with the target system to get more information.
This information help us to gain access to the system (exploit).
Information to enumerate:
- SNMP and DNS information
- Usernames,Group names,Hostnames
- Application and Banners
- Network sharing information and services
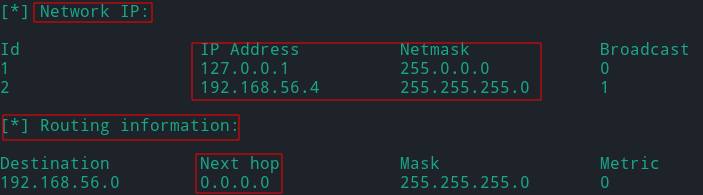
- IP tables and Routing tables
- Services settings, Audit configurations, Web directories
Techniques:
-
Using Email ID
Email ID contains username and domain name in it. -
Using Default password
Using default settings,password and configuration of a device. -
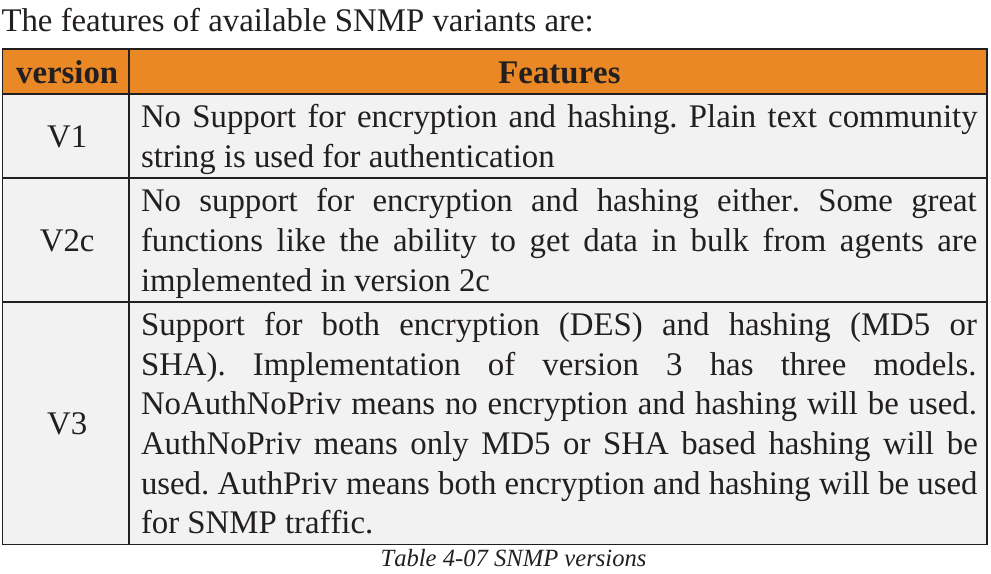
SNMP Enumeration
SNMP (Simple Network Management Protocol) is used for managing network devices.
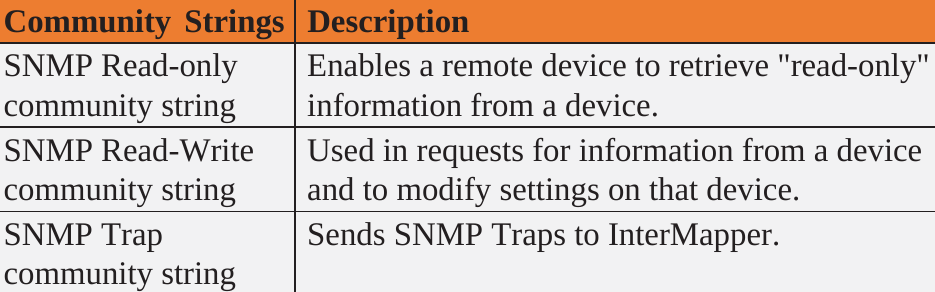
It is used for collecting information from and configuring network devices such as servers, printers, hubs, switches, and routersCommunity strings are used to authenticate devices.
It uses UDP [Ports:161, 162 (Trap)]
Default community strings or guesses can be used to extract information about a device.
Information to enumerate:
- Network resources such as routers, shares, devices, etc.
- ARP and routing tables
- Device specific information, Traffic statistics etc.
Enmuerating SNMP in Metasploitable2
By default SNMP is disabled in Metasploitable2.
Enable SNMP in Metasploitable2
Edit /etc/default/snmpd
and change 127.0.0.1 to 0.0.0.0 and reboot it.
- Using NMAP Scripts
- snmp-sysdescr - Attempts to extract system information from an SNMP version 1 service.
- snmp-info - Extracts basic information from an SNMPv3 GET request.
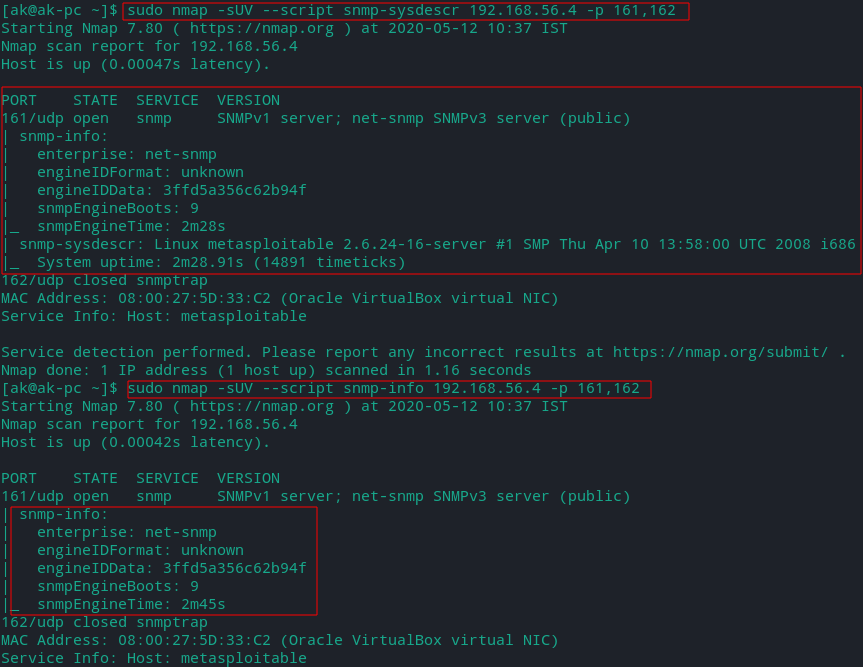
engineID
Every SNMPv3 device has its own ID(engineID). It is a unique number for every context that a agents operates in. But on most of the devices only one SNMP agent runs, so every device has a unique engineID.
snmpEngineTime/Boots
In SMPv3 to protect against replay attacks (when an attacker records the packets and sends it later again towards the destination) the manager first asks the agent how many times it rebooted already (snmpEngineBoots) and how long ago the last reboot was (snmpEngineTime) .The communication is encrypted.
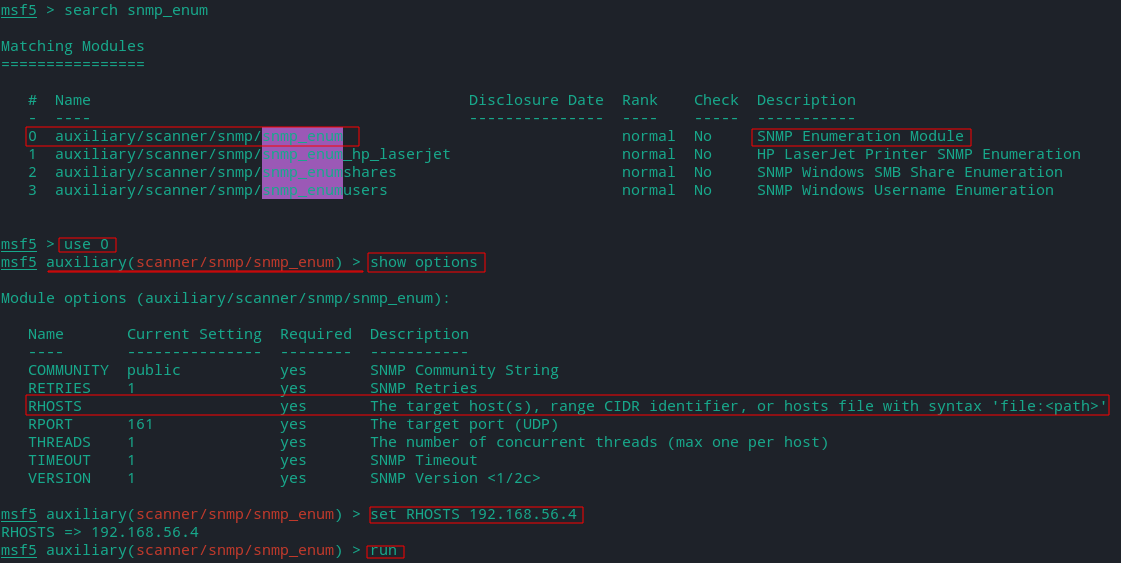
- Using Metasploit Modules
Metasploit Framework includes hundreds of auxiliary modules that can perform scanning ,enumeration and much more.
- snmp_enum
It performs performs enumeration of any devices with SNMP protocol support.
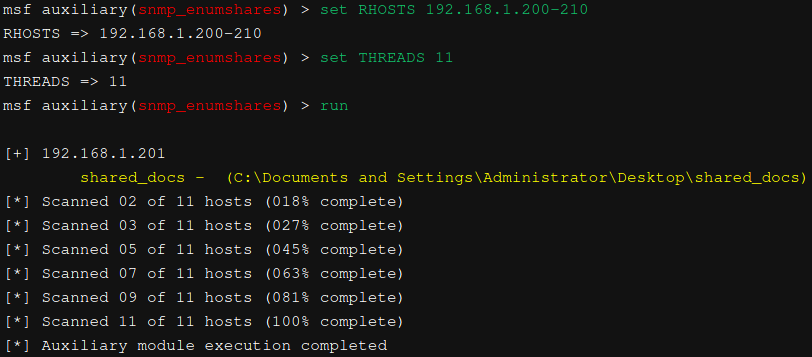
- snmp_enumshares - SNMP Windows SMB Share Enumeration
It determine any available shares.This module is for **Microsoft Windows OS.**This module will use LanManager OID values to enumerate SMB shares on a Windows system via SNMP.
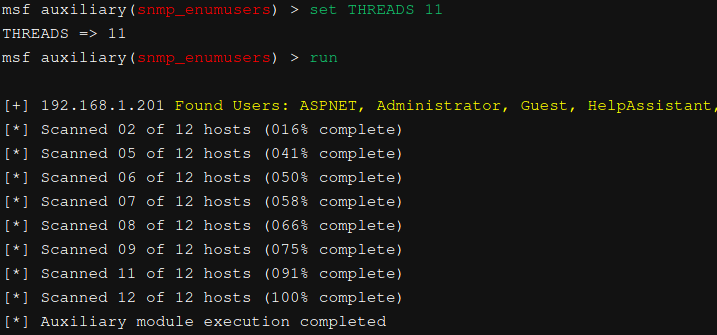
- snmp_enumusers
It gathers a list of usernames on the remote system (Windows/Solaris).
- snmp_login
It scans a range of IP addresses to determine the community string for SNMP-enabled devices by loging in to SNMP devices using default public and private community strings.
It also identify attached devices that are insecurely configured.
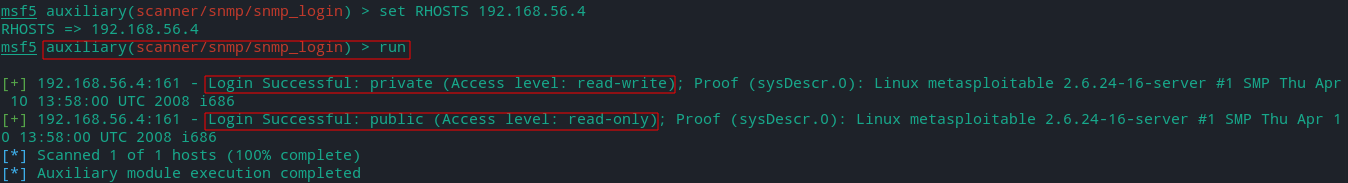
-
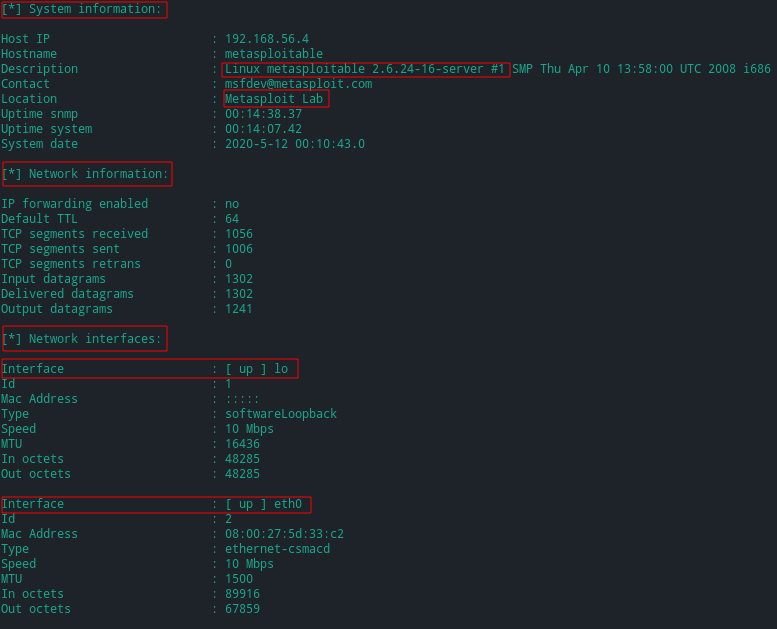
It was able to find both the private community string (set to the default "private") and the public community string (set to the default as "public").
-
These community stings can then be used to grab information from the MIB about the target system.
-
sysDescr(system description) provides the description about the device being monitored.